By Sandra Sieber and Javier Zamora
To be effective in the new world of digital transformation, any organisation needs to address cybersecurity as a continuous effort.
In this article we present a framework to help managers to implement a structured approach to manage cybersecurity in the context of a digital transformation process. Businesses should start with addressing cybersecurity at the highest organisational level by including cybersecurity in business strategy, using secure-by-design principles, ensuring business continuity in case of cyber threat and treating cyber risk as part of a holistic risk management approach.
ƒ
I. A New Environment of High Digital Density
Alarms are sounding louder and louder: with the digital revolution come not only great opportunities and profound changes in the business models of companies of all sectors, but also great threats. One of them, perhaps even the main one, is the lack of security of emerging digital ecosystems. We constantly receive disturbing news about ransomware, denial of service, or data theft. However, it does not seem that companies around the world pay enough attention to them, nor that they are aware of what cyberattacks mean to the smooth running of their businesses.
In fact, it was clearly summed up by Inga Beale, CEO of the insurance company Lloyd’s at the World Economic Forum meeting in Davos in 2017, when she stated that there are currently two types of companies in the world in terms of cybersecurity: companies that know they have been attacked and those that have been attacked but do not know it. This leads us to the inevitable conclusion that if we think that we have not yet been the victims of a cyberattack, we inevitably are part of this second group, living in a fallacious ignorance.
The increase of Digital Density as the percentage of connected data that an organisation uses to create, deliver and capture value leads to an increased complexity of the business. The exponential growth of connections, representative of the 4th Industrial revolution, allows users an easy access to huge amounts of data, which has many benefits for businesses, such as obtaining a greater efficiency or creation of innovative services and products.
However, this digital revolution also carries its dangers. Until recently, only some computers in organisations were connected to the Internet, and the dilemma of data security was simply to protect the digital perimeters of the organisation itself. However, increasing Digital Density has forever changed the playing field: nowadays not only individual devices get connected to the Internet or to other networks, but the whole digital and physical realities are blended. This has exponentially increased the surface of attack of the organisation. Therefore, more than ever it becomes important to treat cybersecurity as the “business function of protecting an institution from the cyber-attacks”, especially considering such constraints as “other business objectives, resource limitations, and compliance requirements”.
In this article, we propose a framework for the management of cyber security as an integral phenomenon in the context of a digital transformation process, which includes designing value propositions using secure-by-design principles, good technical management, the establishment of governance at the highest level, and the active and safe participation of any manager or user in the organisation.
[ms-protect-content id=”9932″]
II. Why look at the cybersecurity issue holistically?
We all live now in a world of high Digital Density, which increases as the number of organisations, people and things get more and more connected. A mere decade since the first smartphone, these connections now number in the billions. As Digital Density intensifies, the once sharply defined lines between the digital and physical worlds begin to fade, forging a new blended environment, in a process known as digital transformation.
The exponential growth of Digital Density creates a unique new terrain, in which digital becomes an environmental factor, spreads beyond the boundaries of the organisation, provides greater transparency and enhances connectivity with the world outside. Digital transformation is accelerated by three main phenomena: consumerisation, democratisation and new business logics:
• Consumerisation means that consumers have access to advanced technologies which change the way consumers interact with organisations.
• Democratisation means that technology innovations translate into a substantial drop of the entry barriers for many businesses by increasing speed-to-market, lowering costs and delivering value proposition more effectively.
• New business logics based on platforms, where the value proposition is the result of the participation of many actors in a given ecosystem.
The above-mentioned processes lead to a substantial shift in many industries: from established linear value chains to complex and heterogeneous ecosystems connecting different actors, suppliers and collaborators that can play a critical role in reshaping business strategy and creating a new value proposition. For organisations to be successful in this new environment of high Digital Density and to embrace digital transformation fully, they need to build a solid IT infrastructure that supports its business strategy and a new organisational model.
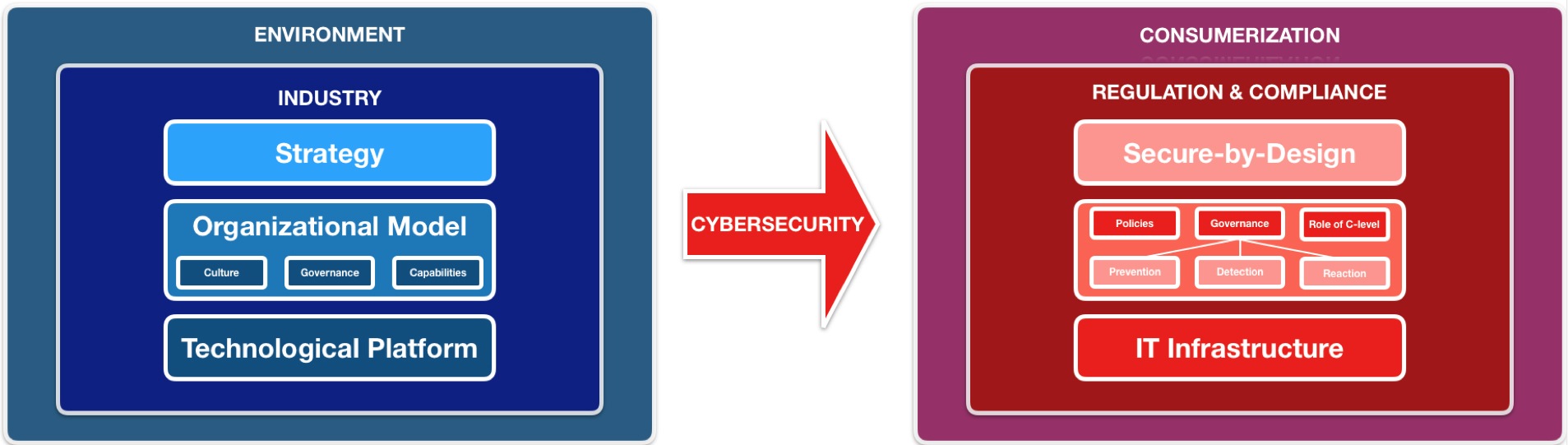
Therefore, in any digital transformation process we usually look at three main business dimensions placed in the context of an industry and environment (Figure 1). Whereas organisations can control internal processes of how their value proposition is constructed and brought to market, there also exist industry and environment specifics (e.g. regulation) that the complexity of the value proposition depends on (complexity of value proposition refers to the complexity of offering, such as products and services, of an organisation).
The three business dimensions are the following:
1. Creating a business strategy that would allow companies to create a fresh value proposition for the market.
2. Establishing an IT infrastructure to support the new business model.
3. Setting up an organisation that is “fit for purpose” in terms of organisational culture, governance and capabilities.
In a world of increasing Digital Density, organisations have an opportunity to enhance their business models and deliver completely new value propositions to the market by using the connected data and the interactions that it offers.
By doing so, organisations can achieve higher automation; use huge amount of connected data to describe, predict or recommend courses of action; build new value propositions by coordinating disparate actors; and create a fully customised product or service for their consumers.
However, these changes also create new challenges that organisations need to recognise and address, related to privacy, integration, reliability and security. The problem of privacy relates to the exponential growth of data, however the ownership of it is not clear and is not fully regulated, therefore businesses have to be transparent in their use of personal data to build trust with their consumers. The integration challenge relates to multiple players taking part in creating a shared value proposition, lack of standards in participating in IoT (Internet of Things) and ways of sharing value derived from the connected data. Another issue in a high Digital Density environment is the reliability of the software and technology. Last but not least, there is the challenge of security derived by the increase of Digital Density as hyper-connected data exponentially increases the surface of a potential cyberattack.
To protect the reputation and build trusting relationships with their customers, who will ultimately influence the sustainability of the business itself, managers have to be aware of all advantages, but also risks that digital transformation brings. Therefore, we cannot treat cybersecurity as a mere mechanism to protect the organisations in the face of new threats, but rather need to regard cybersecurity as an integral part of a digital transformation process. To this extent, we should apply the aforementioned Digital Transformation framework in the context of cybersecurity.
Accordingly, we should focus on incorporating secure-by-design principles into the business strategy, enhancing business processes by focussing on such aspects as culture, capabilities and governance (encompassing three phases of prevention, detection and reaction), improving employee behaviours inside the organisation and establishing robust technological controls (Figure 1). These measures help protect company assets, reputation and the broader ecosystem, including customers, partners and vendors.
In addition to the above-mentioned dimensions, each business operates within the context of a specific industry and its wider environment, which have different regulation and compliance requirements based on the posed risk (e.g., systemic risk, risk to human lives and well-being, etc.), and different levels of complexity of the value proposition (e.g. high complexity of self-driving cars vs. low complexity of value proposition in media industry). Particular aspects of the industry and environment dictate the way organisations conduct business within the market.
Figure 1. Framework for digital transformation (left-side) and its application in cybersecurity (right-side)
III. Business Strategy. Secure-by-Design
The main purpose of a successful business strategy is implementing a business model, which creates and captures value:
• Value creation is related to designing the value proposition, which is aligned with the needs of the customers and is reflected by back-end and front-end activities:
• Back-end activities, or all the key activities, key resources and partners involved to put together the value proposition.
• Front-end activities, or all the activities (delivery channels, customer relationships) organisations put in place to deliver the value proposition to the different customer segments.
• During value capture stage the focus is on the monetising of the value proposition. When capturing value for the business it is important to evaluate potential risks from lack of cybersecurity management (e.g financial risks, reputational risks, etc.) and assess the total economic impact of cyber security processes on the company (see section “Organisational Governance”).
More often than not, new value propositions are the result of multiple interactions of different internal and external actors (partners, suppliers, customers and technology vendors). To that extent, the resulting new products and services also get increasingly connected and that expands the surface of potential attack dramatically. Hackers will target the weakest link. As a matter of fact, half of the breaches originate in an external actor participating in the value proposition. Therefore, organisations should approach the issue of cybersecurity as a broader ecosystem and ensure that all the life cycle of a product or a service is secured, including back-end and front-end activities. Implementing Secure-by-Design principles can help build a digitally resilient organisation and maximise the expected organisational benefits while lowering potential cybersecurity risks.
Whenever a new product or service is designed, every new added feature should be evaluated from the point of view of the communication process, to identify weak points. Additionally, we should question if that given feature should be included by default or as an option. Finally, we should put ourselves in the shoes of a hacker to consider multiple scenarios of abuse of that given feature in order to minimise the surface of attack.
However, organisations need to make a trade-off between protecting the new products and services and achieving high levels of customer experience and usability. These trade-offs will depend on the cost of opportunity of the cyberattack. For instance, customers will accept a stronger control while accessing their bank accounts, which could result in a higher latency in the access of information. Nonetheless, a similar stronger control could damage customer experience and/or customer acquisition in an e-commerce environment. Therefore, businesses should carefully evaluate customer preferences and implement right risk controls without hurting customer experience.
In order for cybersecurity to become an integral part of the product development process, it demands a transversal and tight integration of the product development team with the cybersecurity experts. This new imperative may be challenging as in the past these teams used to work independently and sequentially since cybersecurity usually was considered an afterthought once the value proposition was already developed.
Once the new product or service is already in use by the consumers, establishing data privacy is critical to build trust with them, requiring additional focus on security in the front-end activities. To that extent, it is important for front-end employees to be prepared to address customer questions about security. Training and close cooperation between corporate cybersecurity and sales teams can improve the relationships with concerned customers. Clarifying security issues into contracts with providers and partners will ensure that they share the same commitment to security as your organisation does.
IV. Organisation. Culture, Governance and Capabilities
We hear a lot, that cybersecurity is everyone’s job, but what does that actually mean for an organisation? Below we consider how an organisation should approach such dimensions as culture, governance and capabilities in order to build a proper cybersecurity function.
Culture
Creating a cyber-risk awareness culture in an organisation is an important yet a challenging task as it requires both personal and organisational accountability, as well as, a mind-set and behavioural shift of employees. To that extent, cybersecurity is analogous to what happened with the introduction of quality processes in the 80s. Initially, it was the responsibility of one department, but with time it became an organisation-wide approach.
Well-deployed cybersecurity culture should start at the top of the organisation with senior management and be based on sound employee policies, enterprise-wide communication and raised awareness of cyber threats, training and also reward and recognition schemes.
Senior management serve as role models for an organisation and their commitment is an important start for a culture change. We consider the importance of business leaders’ roles in cybersecurity in the section “Organisational Capabilities” below.
Sound employee policies should provide clear guidance on an organisation’s attitude towards security and ensure that all personnel (including vendors and third parties) understand the ten basic principles of handling personal and company data, which include:
1. Password management and updates
2. Periodic software updates
3. Using original licenses
4. Avoiding public Wi-Fi
5. Distrusting USB keys
6. Not clicking on links
7. Doing back-ups
8. Using antivirus programs
9. Using corporate email
10. Being careful with personal applications
To implement security policies and rules, all employees should respect them and understand the potential consequences of not following procedures. Awareness and communication programs become critical to engage different groups and address their concerns accordingly. Additionally, organisations have to provide the necessary training and tools for employees to follow new behavioural paths and learn how to deal with security issues at work. Systems of penalties and incentives may reinforce security messages in an organisation, which, in turn, will create a stronger cybersecurity culture.
For an organisation’s security strategy to be successful, employees and third parties have to be fully engaged and share the common understanding of what cyber secure culture means.
Organisational Governance (Prevention, Detection and Reaction)
A strong cybersecurity governance should address day-to-day operations and internal business processes. It should provide real-time risk management with solid prevention, detection and reaction mechanisms. Moreover, it should bridge the physical security, information security, business continuity, and crisis management protocols to minimise the risks and eliminate duplication of processes or creating silos.
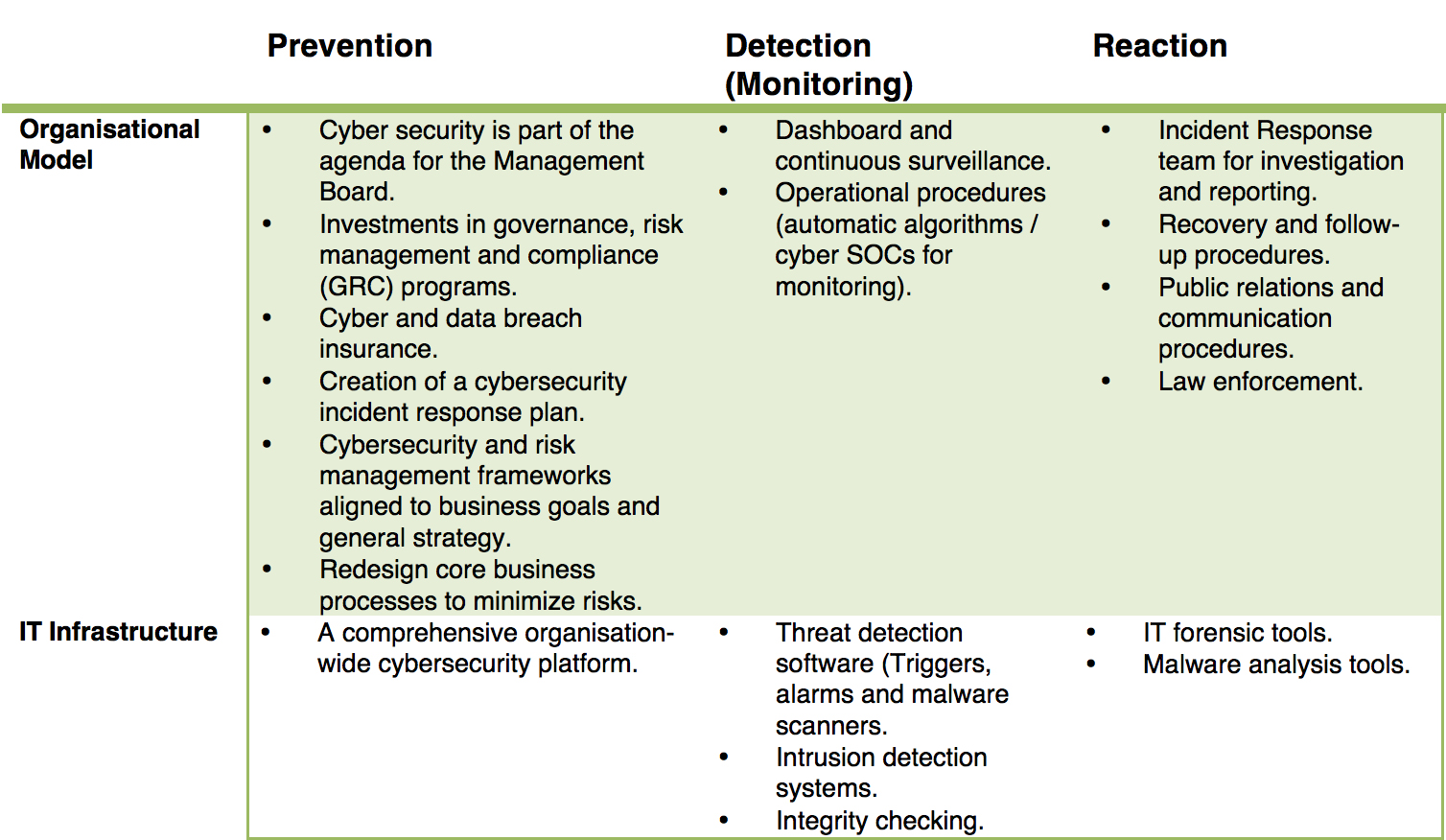
The organisation must work on three main fronts. Firstly, try to reasonably protect the organisation from cyberattacks (prevention). Secondly, have mechanisms for an early detection of cyberattacks (detection). And thirdly, have a rapid response system with ways of containing damage and restoring normality of business after an attack occurs (reaction). Table 1 outlines the main mechanisms used in prevention, detection and reaction stages.
Table 1. Prevention, detection and reaction activities
Ensuring that cyber risk programs prioritise the relevant threats, outlining initiatives to minimise risk and continuously fine-tuning business-continuity and crisis plans would help business get ready in the event of data breach.
Prevention
Prevention actions should provide risk mapping (categorisation, classification, and taxonomies) for cyber threats, so an organisation can assess risk, vulnerability, and prioritise actions. Investments in governance, risk management and compliance (GRC) programs help evaluate risks across the business and can improve an organisation’s ability to detect and escalate a data breach. Due to the changing nature of cyberattacks, the organisation should re-evaluate periodically all business processes by identifying new potential security issues, whether it requires re-designing core processes or establishing additional controls where needed.
As connected data is becoming the main asset of a company, it is imperative to classify all data based on its sensitivity. Users should be segmented following the “need to know” principle, in particular only allowing access to the most important data to trained users and providing third parties with the minimum information needed only. In addition, consumerisation translates into another security challenge which appears when employees demand access to corporate networks through their personal mobile devices. Employee monitoring, although it may sound paternalistic, is necessary to ensure the safety of an organisation. It may include regular risk assessments of vulnerable employees and networks, monitoring outgoing traffic or installing malware detection systems. Among the main causes of a data breach are malicious or criminal attacks, system reliability or human error. A strong end user education, including practices for handling data and recognising phishing attempts, should also be among preventive measures for the business. Most importantly is the need to provide customised training and attend to particular employees’ behaviours and deal with them, rather than teaching generalised principles.
In a world of high Digital Density, the value proposition is the result of the participation of many actors interconnected in an ecosystem. To that extent, special attention should be given to the partner and provider selection to ensure that their cybersecurity practices are aligned with the standards of the organisation.
Besides the above-mentioned prevention techniques, organisations should invest in a cyber and data breach insurance, which can help manage the financial consequences if an incident occurs. The “2017 Cost of Data Breach Study” by Ponemon Institute shows that insurance protection and business continuity management reduced the cost of data breaches following the discovery of the incident. Business continuity can be ensured by developing a written cyber incident response plan that outlines cyberattack scenarios and sets out appropriate responses. Having a well-outlined incident response plan will help to identify and act on the data breach quicker, which will lower the total costs of the breach. An incident response team should be supplied with all tools necessary to analyse the breach and act on it quickly.
Detection (Monitoring) of breach incident
Detection and monitoring actions normally would include investigative activities, understanding the type of attack, an assessment and audit services.
Investigation would allow the company to:
• Gain a fuller understanding of a computer or any connected device (tablet, smartphone and IoT) intrusion.
• Increase its chances of identifying the attacker.
• Detect previously unknown security vulnerabilities.
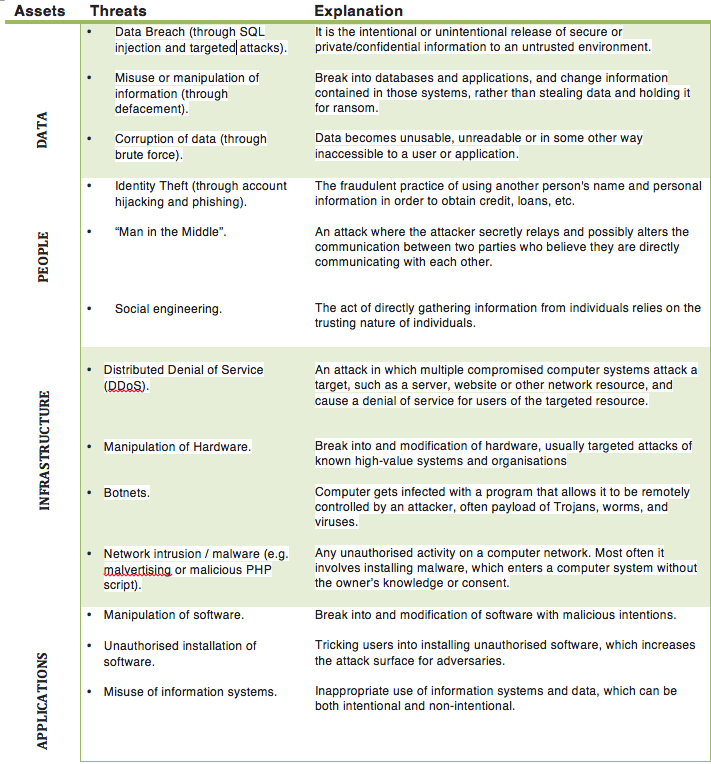
Cyber risk exists on different levels and targets different assets, such as data, infrastructure, people and applications. In order to help detect a breach incident it is useful to understand a taxonomy of cyberattacks and classify responses according to most common cyber threats.
Table 2. Types of cyber threats (adapted from the McKinsey article “A new posture for cybersecurity in a networked world”, March 2008 and European Union Agency for Network and Information Security ENISA & The SANS Institute)
This list (Table 2) represents the identified attacks and techniques. However, the most disturbing fact is that currently over 40 percent of attacks are of an unknown nature. Breaches occur, not because a defense solution is inefficient, but because adversaries find ways to penetrate networks in-between the very tools, processes, and teams put in place to keep them out.
Reaction to a breach incident and recovery
Consequences of cyber-attacks can seriously affect the value capturing of a given business model. In a recent McAfee report, the cost of cybercrime accounted close to $600 billion per year, or 0.8 percent of global GDP. This is up from a 2014 study that put global losses at about $445 billion.
The consequences of a cyberattack could be the following:
• Financial losses and direct damage to revenues.
• Lengthy processes of restoring the data and reputation.
• Legal proceedings.
• Indirect damage, such as reduced operational efficiency, lower employee morale, or broken customer relationships.
• Catastrophic consequences for society (e.g. hacking an industrial plant or furnace explosion).
Therefore, the right reaction to a breach incident is as important as the prevention and detection of an attack. Besides cleaning up the hacked system and restoring the “day to day” operations, it is important to conduct a thorough investigation led by the crisis incident response team and communicate results to executive management, board of directors, vendors and customers.
Upon restoring computer (or any connected device) systems, the company should aim at repairing the affected systems and bringing the repaired systems back online timely. However, it is also important to update the cybersecurity plan to prevent similar incidents from reoccurring and evaluating how the response team executed the response plan.
It is also important to execute well-thought external activities, which should cover informing the consumers and clients as well as sharing learning points from the breach with industry experts and authorities. The cyber incident response plan may outline how press releases and other public announcements about the cyberattack should be handled. While addressing customer or end user concerns in an adequate way may help restore consumer confidence and loyalty (for example after theft of a credit card), sharing with experts and authorities will create a solid ground for joint resistance to future cyberattacks.
Capabilities
When a sophisticated corporate governance structure exists, certain attention should be paid to the capabilities within the organisation:
• Clearly defined roles of line-management responsibility and accountability throughout the organisation (between headquarters, regional teams and subsidiaries).
• Transparent decision making at all levels throughout the organisation.
The biggest differentiator of a company’s preparedness for a cyberthreat is engagement by the board in cybersecurity, yet, according to an IBM survey, not all members of the C-suite feel equally engaged in cybersecurity. For example, CFOs, CHROs and CMOs report they do not feel prepared for cyber threats, though these roles own the data most desired by cybercriminals. So, which behaviours could C-level executives adopt to ensure that the company is well-equipped in a cyber space?
Role of CEO is critical in creating a risk-aware culture among executives and across the entire organisation by executing the following actions:
• Ensuring that the board regularly receives security briefings and incident reporting and understands them.
• Treating cyber risk as a risk management issue, not an IT problem and demonstrating that cybersecurity principles are the top priority.
• Using collaboration both internally and externally to manage threats and secure the organisation’s most valuable digital assets.
While creating cybersecurity frameworks and implementing technical solutions is in the hands of CIOs and their teams, right compliance behaviours and communication to the rest of organisation should start with CEOs.
Role of CIO (CSO, CISO, or CDO) is to prove that investment provided by the business goes to strengthen cybersecurity risk programs by setting up policies and procedures for employees and to monitor the occurrence of cyberattacks. It might be difficult to make comprehensive risk assessments of cyber space activities as a large portion of those have an unknown nature. However, CIOs should ensure a comprehensive cybersecurity framework exists, which also covers for a rapid response as cyberattacks will still happen despite the best efforts. To that extent, CIOs should:
• Ensure the organisation-wide cybersecurity framework is connected to general business strategy.
• Learn the most effective way to communicate with core executives to ensure cybersecurity is on the Board’s agenda. Behavioural science research offers a number of approaches to build more effective communication with C-suite. For example, CIOs could use clear narratives when talking to senior executives and shift executives’ focus from building the right system to building the right process.
• Apply metrics that would evidence cybersecurity improvements, such as allowing “white hat” hackers to search for vulnerabilities in the system and reporting the number of faults they have discovered.
Role of the rest of C-suite is to engage into cybersecurity topics, collaborate with IT on managing a good cyber “hygiene” in their respective departments by means of implementing and enforcing data security and privacy policies, procedures, and controls to help minimise potential damages and reduce the chances of a data security breach.
V. IT infrastructure
A solid IT infrastructure is the basis for implementing cybersecurity policies in any organisation. Strong architectures for data, systems, and security should be established to ensure “security by design” and to build long-term digital resilience.
Traditionally IT systems provided security within an organisational perimeter, however nowadays many organisations migrate its data to the cloud and even physical value propositions (e.g, car, home automation, etc.) are connected through the proliferation of IoT. This new scenario requires an utterly new security model. To address the challenges of The Fourth Industrial Revolution, forward-looking companies have to protect organisational roles and data rather than devices. It requires new and creative ways in approaching data protection, like distributing sensitive information over several databases or restricting access to only a limited number of employees.
IT infrastructure should be up-to-date and require investments in the right technologies. IT in house efforts should also include:
• Having the company’s database on a different web server than the application server.
• Applying the latest security patches.
• Protecting all passwords.
• Using read-only views of documents and materials when possible.
• Maintaining strict input validation.
• Developing network security architecture.
• Encrypt sensitive data.
• Monitoring activities and procedures of third-party contractors with access to the computer system (whether direct or remote).
• Performing network scans to assess activity on the network.
• Comparing outbound network traffic to baseline operations.
• Choosing names for tables and fields that are difficult to guess.
• Having up-to-date intrusion detection and prevention systems (IDS/IPS).
Introducing a comprehensive enterprise-wide cybersecurity platform can offer visibility across the high volume of security data. By having a threat management system providing security event monitoring, cybersecurity teams can quickly, accurately, and measurably identify, prioritise, and respond to threats, and also secure company and customer data.
Besides that, companies can begin to use Artificial Intelligence (AI) to detect cyberattacks and react to data breaches. However, simultaneously AI is deployed by hackers, which brings cyberattacks to a more sophisticated level. This increases the importance of investing more into cybersecurity’s newest technology.
VI. Conclusion
In the current world of increased Digital Density there are three main reasons why organisations currently struggle with cybersecurity.
First, it is due to not including cybersecurity into organisational strategy and struggling to provide a valid business case for cybersecurity investments as probability of any given attack and potential costs are unknown. Cybersecurity often gets treated as a “problem to be solved” by the IT Department rather than as the ongoing iterative improvement process, which in turn leads to uninformed choices and heightened risks for the business. Second, it is due to not having any sophisticated governance frameworks, practices, policies and capabilities in place to secure the business. Third, organisations are at a high risk of breaches when they do not invest in IT infrastructure and do not extend security processes to third party providers, partners, vendors and consumers, which are outside of the “perimeter of an organisation”.
In this article we offered a framework, which addresses the above-mentioned challenges and allows managers to implement a structured and sophisticated approach to managing security in their organisations. Businesses should start with addressing cybersecurity at the highest organisational level by including cybersecurity in its business strategy, using secure-by-design principles, ensuring business continuity in case of cyber threat and treating cyber risk as part of a holistic risk management approach.
Concurrently companies should establish a fit-for-purpose organisation by educating every member of the organisation to behave in a cyber-secure way, building right capabilities throughout the organisation and introducing a sophisticated governance framework with solid prevention, detection and reaction mechanism.
Finally, cybersecurity should be based on a solid technological base to protect the organisation, therefore the IT department should be aware of recent developments in defending business systems against cyber criminals.
To be effective in the new world of digital transformation any organisation needs to address cybersecurity as a continuous effort that requires dedication, efforts and senior management involvement and include cybersecurity principles from the very beginning when designing an organisational structure, product or service.
[/ms-protect-content]
About the authors:
 Sandra Sieber is a Professor of Information Systems at IESE Business School. She holds a Ph.D. in Management from IESE and a Degree in Economics and Business Administration from Universitat Pompeu Fabra. Currently, most of her work is centred on how the digital rise is affecting organisations from a variety of perspectives.
Sandra Sieber is a Professor of Information Systems at IESE Business School. She holds a Ph.D. in Management from IESE and a Degree in Economics and Business Administration from Universitat Pompeu Fabra. Currently, most of her work is centred on how the digital rise is affecting organisations from a variety of perspectives.
 Javier Zamora is a Senior Lecturer of Information Systems at IESE Business School. He holds a Ph.D. in Electrical Engineering from Columbia University and a M.Sc. in Telecommunications Engineering from Universitat Politècnica de Catalunya. His current areas of interest are focused on how high digital density is transforming organisations and sectors.
Javier Zamora is a Senior Lecturer of Information Systems at IESE Business School. He holds a Ph.D. in Electrical Engineering from Columbia University and a M.Sc. in Telecommunications Engineering from Universitat Politècnica de Catalunya. His current areas of interest are focused on how high digital density is transforming organisations and sectors.
References:
1. James Kaplan and others. (2015). “Beyond Cybersecurity”, Wiley.
2. Zamora, J. “Programming Business Models Through Digital Density”, IESE Insight, 2017, Issue 33 (ART-3013-E).
3. S. Sieber, J. Zamora, D. Daswani and S. Gil. (2016).“La Ciberseguridad en la empresa: decálogo de buenas prácticas.” IESE-Deloitte Draft Document, June.
4. McAfee Report, in partnership with the Center for Strategic and International Studies. (2018). “Economic Impact of Cybercrime – No Slowing Down”. February.
5. IBM Institute for Business Value. (2016). “Securing the C-Suite: Cybersecurity perspectives from the boardroom and C-suite.”
6. S. Durbin. (2016). “The C-Suite Gets Serious About Security.” CIO Insight, February.
7. Chief Security Officer (CSO), Chief Information Security Officer (CISO), Chief Data Officer (CDO).