Ransomware is computer software which effectively blocks access to files until money is paid to restore access. It can be delivered by an infected email, downloaded from a compromised website, or even dropped into a computer system by hackers. In recent years, cases of ransomware have increased and their effects have become more complex. Here are three types of ransomware to look out for:
Ryuk
Ryuk first appeared in 2018 and targeted industries sensitive to a lack of computer access. This included healthcare, newspapers, and even a public water utility company. Believed to be derived from North Korea’s Lazarus Group, Ryuk was most likely built on Russian code. Ryuk effects the computer’s system by encrypting data which it systematically selects. It also disables the Windows System Restore function, preventing the operator from simply restoring the computer to a backup date prior to the infection. It then generates a ransom note in a .txt file demanding payment for the decryption of the data.
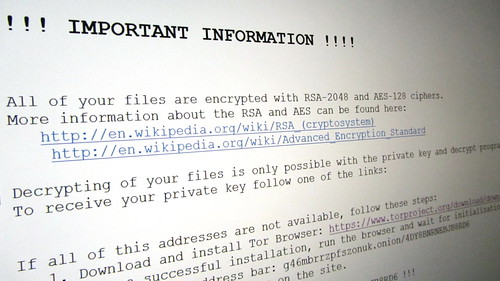
WannaCry
Spreading across Europe in May 2017, WannaCry ultimately shut down computers from several organizations worldwide. The attack included large firms in Spain, school systems in multiple Asian countries, a French car maker, an American shipping company, and many others. On the initial day of the attack, it was estimated that 75,000 computers in 99 countries were affected. Russia and other European countries were deemed the hardest hit.
WannaCry took advantage of a security loophole in the Server Message Block protocol of Microsoft Windows. While a patch was released for newer versions of Windows, many organizations were still running older versions of the operating system that no longer received regular security patch updates. These systems were particularly vulnerable. Like the Ryuk virus, it encrypted computer files and demanded payment for the encryption to be reversed.
On May 13, 2017, Microsoft released an emergency security patch to stop WannaCry from affecting these older systems. The patch also included a kill switch which stopped the ransomware from spreading to other machines.
SamSam
Dating back to 2015, SamSam focuses on specific organizations, infiltrating their systems to determine security weaknesses. Once the system is accessed, privileges for file access are all elevated before the files are encrypted. By doing this, it becomes more difficult for the decryption to occur.
Unlike other ransomware, SamSam targets multiple different file systems depending on where security weaknesses are found. Ultimately, SamSam attacked several organizations, including a state department of transportation and several healthcare systems. Because of how SamSam evaluates a system before the attack is launched, it is less vulnerable to endpoint anti-virus and security software. There are several ways to protect yourself from a ransomware attack. Obtain an email scanning program and use a secure email gateway to detect and defend against phishing and spam emails. A secure web gateway can be used to prevent malicious content from being downloaded from a compromised website. Install antivirus software and keep your virus definitions updated. It is also a good idea to keep a complete and updated system backup.


































