By Gregory Gimpel and Allan Alter
Companies are introducing “smart products” and deploying sensors into the environment, intent on gaining data-driven insights. Although often framed as the future, most industrial companies can benefit from Industrial Internet-of-things (IIoT) data without spending a fortune on creating an ecosystem of new and connected instruments. Many firms can benefit by tapping into the vast amounts of data generated by their operational technology, transactional systems, and other equipment. Concerns about data breaches, customer trust, unauthorized data use by partners, as well as an uncertain legal environment cause many firms to remain on the sidelines rather than leveraging the extensive data they already generate. This article presents strategies for overcoming there challenges.
Companies increasingly are introducing “smart products” and deploying sensors into the environment, intent on gaining data-driven insights for improving operational efficiency and delivering better services to their customers. While some companies are launching cutting-edge Industrial Internet-of-things (IIoT) initiatives, most industrial companies can benefit from IIoT data without spending a fortune on new technological ecosystems. Most of these firms can benefit by tapping into the vast amounts of data generated by their operational technology, transactional systems, and other equipment1. As with new IIoT initiatives, these existing data can be analyzed to improve processes and provide competitive advantage, but at a fraction of the cost and with considerably less lead time.
Unfortunately for most organizations, these data remain unused, or “dark.” This “dark data” remains unanalyzed, despite offering opportunities to leverage IIoT insights right now2. Even when companies are made aware of dark data’s usefulness, few take advantage of the data-driven opportunities it offers. Similar to other IIoT initiatives, questions about data management impede many companies from exploiting their dark data. Cybersecurity concerns create substantial roadblocks. Uncertainty about how partners and customers will react to having their data from current operations stored and analyzed also inhibits many companies from taking full advantage of the data they have. Additionally, as technology outpaces the law, companies face unanswered questions about whether certain uses of dark data are even legal.
Data hacks and other unauthorized access pose existential threats to many businesses. In today’s connected world, if you are connected, you can be hacked. Hackers can wreak havoc in all sorts of ways. The president of a large machine tool supplier shares an example of how cybersecurity concerns are paralyzing efforts to bring dark data into the light.
“In this case, we wanted to be able to diagnose issues with the machine tool remotely. It was very simply a connection through their intranet, through their server, to connect to the machine so they could call up the conditions on the control at that time. But they would not allow us – either through a separate one with a cellphone-type connection or hard-wired – to do that because they didn’t want to take a chance that anybody else would be able to get into their system.”
Hackers are not the only cybersecurity concern. Companies are also facing concerns about how to govern how data will be used by their strategic partners. Once you give access to data to a customer or partner, can you revoke it? Or will they always have access to the data, even after the originally intended time period or project is over? Will partners use the data in unauthorized ways? Will partners maintain confidentiality?
The challenge of managing data extends beyond protecting it from unauthorized access. Questions about how customers will react to the use of their data keeps can prevent companies from using the data to create better customer experiences. For example, consumer goods companies spend billions building their brand reputations. A senior data analyst for a leading consumer products company explains: “But first and foremost is the consumer trust. We have to earn that. So we can’t do anything with the data that comes anywhere close to something that would violate any privacy agreements we have with consumers or anything like that.”
Governance of dark industrial IoT data extends beyond preventing unauthorized access and preserving company reputations. Effective governance must also prevent unlawful data use. Because technology outpaces the law, the legality of bringing dark data into the light is in question. Privacy protection laws differ country-by-country and can change province by province. The Senior Director of Data Science at a large global insurance company explains the challenge: “there are all these data rights and users’ rights which come into play here. We are stepping into something we quite don’t know what it’s going to be, but we know that it’s something new, especially with the interpretation of data and having the rights to use data in more than one way. That’s definitely something which is new and actually nobody knows how to deal with it right now.”
The director of an analytics think tank summarizes the legal concerns that are preventing many firms from exploiting their dark data: “There is a definite advantage to using the data they’ve already collected in new and different ways. But it’s not as simple as doing that. There are issues around making sure you’re not violating some law. That’s #1 that comes to mind. I don’t want my executive to end up in court because they used somebody’s data the wrong way.”
Improving Governance
Concerns about data security, customer approval of data use, and an uncertain legal environment prevent many firms from unlocking the power of their dark data. Thankfully, the executives participating in this study have identified strategies to help navigate this challenging environment.
Reducing Cybersecurity Risks
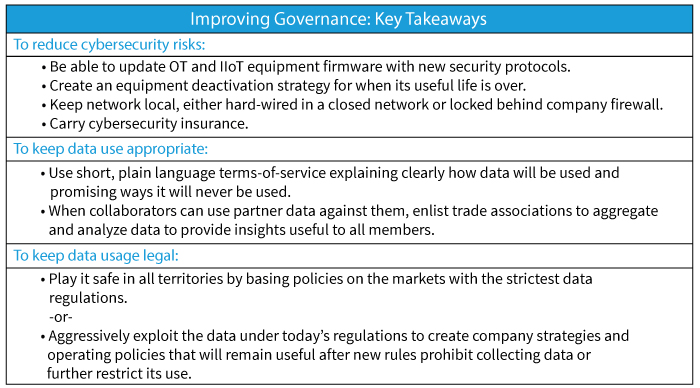
Connecting via the Internet provides the greatest level of accessibility but also provides hackers with the most points of entry. Traditional data security measures such as strong encryption and access controls provide a solid foundation for collecting and analyzing dark data. But since operational technology and Internet-of-things devices may be in the field for many years, even decades, even strong encryption and security protocols quickly grow obsolete. It is imperative to be able to remotely update the firmware during the life of the devices. Therefore, implementing a formal technical strategy for refreshing the security on the equipment will help mitigate some of the security concerns that are preventing companies from making use of dark data. Additionally, by including a useful life protocol when creating equipment maintenance plans, firms will have plans to deactivate equipment once security patches become ineffective.
While broad connectivity offers the most potential, it may not be suitable for some companies. Instead, those companies can use a closed network that sends data to a local computer that is not accessible from the outside. This can be useful for information that must remain a guarded secret. The principal researcher at a precision measurement company explains: “When we installed our system on a machine at a defense contractor, they insisted that we set up a separate PC, completely isolated, not put on their network, to do the collection of the data and the data processing.” A less restrictive approach is to connect data-generating equipment within a company’s local area network. The data remains behind company firewalls and is never exposed to the open internet. These two strategies allow for companies to start bringing their dark data to into the light while reducing the cybersecurity risks.
In addition to technical solutions like firewalls, encryption, etc., companies can get cybersecurity insurance. Insurance companies such as AIG, AON, and Zurich offer insurance against cyber breaches, transferring the risks of operating losses, product liability for hacked products, third party claims arising
from the breach, and protection against the fallout if a partner who is using your data gets hacked. While not a substitute for thoughtful technological measures and internal cybersecurity policies, insurance adds an extra layer of protection for businesses.
Using Data Appropriately
Companies who wish to build customer trust are well served by being clear about how they intend to use the data. They should make a few key promises to assuage their customers and offer clear, simple policy rules that can be explained in a few bullet points. Few customers read lengthy terms of service, and such legal agreements increasingly are being invalidated when challenged in court. Even if the legalese holds up, violating consumer expectations erodes customer trust in the brand. Therefore, the uses of data should be clear, specifically stating the ways data may be used without vague blanket-use language. While this may preclude new uses of data in the future, it can help open the window to using data today.
Trust can be strategically advantageous for supply chain partners. One way to build stronger relationships is to share information about demand and logistics, so partners can improve demand forecasts and improve just-in-time operations. It also makes sense for firms within an industry to pool certain types of data to establish best practices or create insights on how to extend the lifespan of their equipment.
Still, there will always be the risk that once a company has data from other companies, it may use it in unauthorized ways. Perhaps a company will mine a collaborator’s data for insights that it can use to its advantage during a future contract negotiation. Perhaps it will combine the data with data from other partners to generate insights that it doesn’t share with its partners.
Within many industries, trade associations already help advance the interests of their members by analyzing data. These trade associations can bridge the trust divide as they already aggregate data to create sales reports, trend analyses, and other useful information. They can act as the trusted, neutral data aggregator that turns the dark data from its members into insights that everyone can use.
Keeping It Legal
Companies should not let the uncertain legal environment covering data collection and use stop them from leveraging their dark data. Instead, they should commit to a strategy.
One potential strategy is to play it safe. Companies can adopt the most restrictive regulations and legal policies in the marketplace. For example, adopting GDPR regulations for other markets reduces the likelihood companies will have to dramatically change their policies in the other jurisdictions.
Playing it safe reduces risk and uncertainty. It does not eliminate it. Laws are still going to change. Rules will still vary among different territories. An alternate strategy is to adopt a policy based on current rules for each market with the expectation that rules about data storage and use will be in flux. The goal is to get insights to develop strategies and policies before legal changes preclude certain types of analysis or new regulations force mass purges of database records. Firms can continue to incorporate and benefit from the data-driven insights long after they have deleted the actual data.
Companies can more affordably benefit from the Industrial Internet-of-things by tapping “dark data” from existing equipment. Concerns about data governance hold companies back from capitalizing on the opportunities afforded by this existing IIoT data. By focusing on governance to reduce the risk of data hacks and unauthorized data use, and to navigate an uncertain legal environment, executives seeking to capitalize on dark data can address the concerns of their customers and their fellow business leaders.
About the Authors
 Gregory Gimpel is a clinical assistant professor of computer information systems at Georgia State University. Prior to GSU, he conducted digital strategy research at the Massachusetts Institute of Technology and he designed Ball State University’s business analytics major. His research focuses on the intersection of emerging technologies, analytics, and digital business transformation. He holds a Ph.D. from Copenhagen Business School and an MBA from University of Southern California. He worked in senior management positions for a decade before entering the academic world.
Gregory Gimpel is a clinical assistant professor of computer information systems at Georgia State University. Prior to GSU, he conducted digital strategy research at the Massachusetts Institute of Technology and he designed Ball State University’s business analytics major. His research focuses on the intersection of emerging technologies, analytics, and digital business transformation. He holds a Ph.D. from Copenhagen Business School and an MBA from University of Southern California. He worked in senior management positions for a decade before entering the academic world.
 Allan Alter is a Digital Fellow at the MIT Initiative on the Digital Economy. He is a former senior principal at Accenture Research and Fellow in Artificial Intelligence and Machine Learning at the World Economic Forum’s Centre for the Fourth Industrial Revolution in San Francisco. His research focuses on emerging technology and technology management strategy. He was previously an editor at MIT Sloan Management Review, Computerworld, CIO and CIO Insight. He holds degrees in intellectual history from the University of Michigan and the University of Pennsylvania.
Allan Alter is a Digital Fellow at the MIT Initiative on the Digital Economy. He is a former senior principal at Accenture Research and Fellow in Artificial Intelligence and Machine Learning at the World Economic Forum’s Centre for the Fourth Industrial Revolution in San Francisco. His research focuses on emerging technology and technology management strategy. He was previously an editor at MIT Sloan Management Review, Computerworld, CIO and CIO Insight. He holds degrees in intellectual history from the University of Michigan and the University of Pennsylvania.
References
1. Stracener C, Samelson Q, Mackie J, Ihaza M. The Internet of Things Grows Artificial Intelligence and Data Sciences. It Professional. May-Jun 2019;21(3):55-62.
2. Gimpel G, Alter A. Enter the Industry 4.0 Era Today by Using “Dark Data” You Already Have. The European Business Review. 2019;July – August:17-20.