By Tom Patterson and Laura Converso
Leaps in quantum technology and hybrid approaches are shortening the time to Q-Day, when adversaries can use quantum computing to break cryptography and threaten data safety for all organizations. It’s hard to predict exactly when this will happen. But given the pace of the development of quantum computing, experts agree that companies need to start implementing a post-quantum defense now.
KEY TAKEAWAYS
- As of today, there are no large-scale quantum computers available that could break cryptographic algorithms, but we know they are coming. Due to the time it takes to implement and promulgate a defense, businesses should act now to counter this threat.
- European businesses should start by putting in place a post-quantum security strategy, a migration roadmap, and a course to crypto agility – the ability to easily move from one algorithm to another. The quantum threat makes crypto agility a recommended choice for post-quantum cryptography transition. And, given that we expect these algorithms to continue to evolve, being crypto agile even after that is also important.
- European businesses waiting too long to complete their migration could pay a high cost or even disappear if they are unable to keep data safe and protected.
Quantum computers will crack encryption – but when?
Today’s hyperconnected world of trade and finance stands on the trust that digital information is protected and can be stored and exchanged safely across the globe. However, even as cyber-attacks become more sophisticated and the security landscape more difficult to navigate, a new and more foreboding threat is on the horizon: quantum computers that have the potential to break cryptography.
Quantum computers will bring many benefits but also pose a serious threat to today’s digital security due to their ability to factor numbers into primes much faster than classical computers.
How immediate is this threat? On January 4, 2023, a group of Chinese scientists claimed that RSA encryption (the public-key cryptosystem widely used for secure data transmission – see inset box “Math problems affecting the real world to know more) could be broken using a quantum computer with only 372 qubits1, a task that experts estimate classical computers would take 300 trillion years. After 48 hours of tension, when companies felt vulnerable and unprotected, other international cryptographers discovered faults in the specifics of the math. Despite the failure of this approach, it highlighted both the international race as well as clever new ways to use early-stage quantum computers for decryption and emphasizes the urgency to get ready.
Math problems affecting the real world
Two proven algorithms – Shor’s and Grover’s – provide the mathematical foundations for quantum computers’ threat to current encryption. While Shor’s algorithm could be used to target asymmetric key cryptography, Grover’s could impact symmetric key cryptography (see figure 1). Both algorithms were developed in the 1990s when quantum computers could only be envisioned in pen and paper. Only recently have quantum machines become a reality, posing a real threat to businesses.
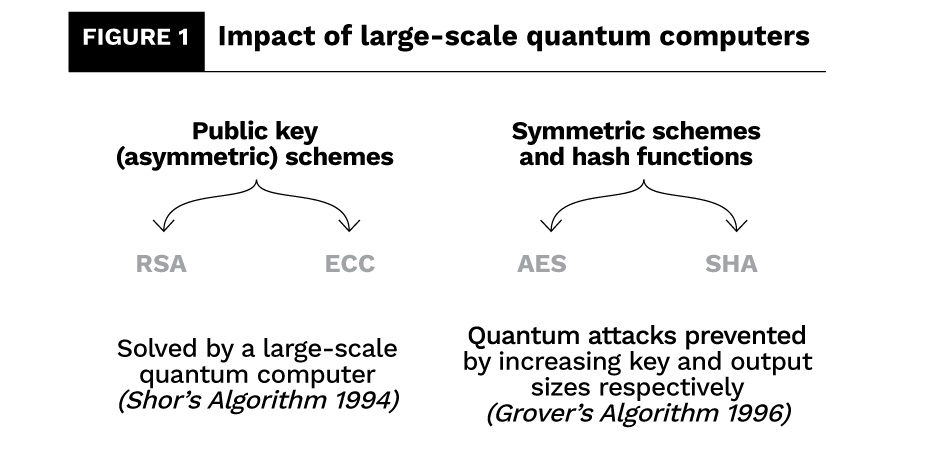
Public-key encryption schemes
RSA-based encryption makes it possible to exchange data via the cloud, deliver digital products and services and communicate with customers.
ECC-based encryption serves to secure the communication on the Internet of Things.
Year 2030: An estimate for Q-Day
The error-prone quantum computers available today do not have the scale to break encryption, but this technology is advancing so fast that things are expected to change soon.
An estimate from experts in post-quantum cryptography (PQC), led by mathematician Professor Michele Mosca, suggested it would take an average of 15 years before quantum computers break the security.2 The calculation first emerged in 2015, so the estimate hits the calendar in 2030.
In Professor Mosca’s3 useful framework to help organizations determine a plan, the urgency to initiate the migration depends on a company’s evaluation of three simple parameters:
- is shelf-life time: The number of years business data must be protected.
- is migration time: The number of years needed to safely migrate a business security system.
- is threat timeline: The number of years until large-scale quantum computers become available.
This simple theorem suggests that if A+B > C, then businesses will be at risk.
The timeline for C is, therefore, not set in stone: 2030 could be too early or too late depending on how fast quantum machines evolve.
Even if the threat seems unpredictable, businesses need to get ready now. Not only because we see quantum getting closer, but also because there is the real danger that someone can store encrypted data today and then decrypt it when such a quantum computer becomes available. In fact, the uncertainty surrounding the precise date makes it hard for businesses to discern the right time to act.
How soon do we need to worry? Not wasting any time, the Cloud Security Alliance4 took 2030 as a valid date for Q-Day and set a countdown clock. At of the time of publication, businesses in the cloud have six years, 260 days, 16 hours and 30 minutes to migrate to quantum-safe security.
Year 2024: Post-quantum cryptographic standards
In all this ambiguity, only one thing is certain – new crypto algorithms are needed to protect our systems against the quantum threat.
Professor Mosca’s theorem published in 2015 formed part of the justification for the US National Institute of Standards and Technology’s (NIST) to begin identifying PQC algorithms that could protect data following the advent of quantum computers. After six years of careful consideration and several rounds of competition, the NIST5 recently announced four candidate algorithms for standardization (see figure 2).
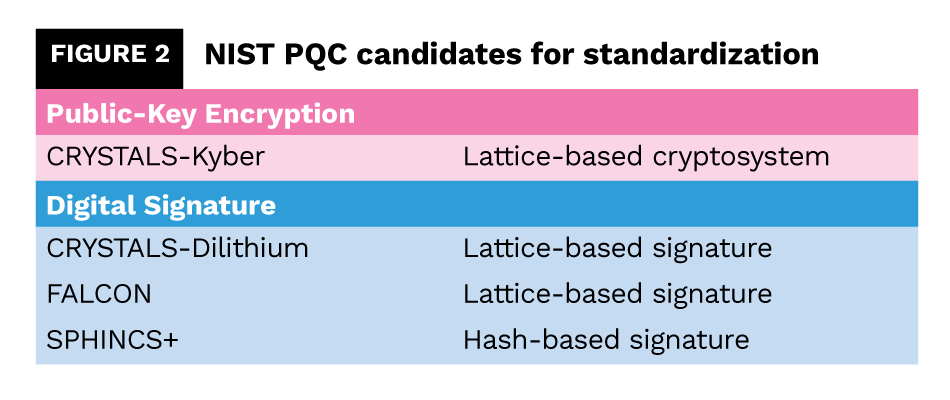
Between now and 2024, NIST will continue to assess technical considerations for the four selected PQC algorithms while identifying alternative options in case advances in cryptanalysis threaten their long-term viability. Lattice-based cryptography is a favorite because no one has developed a quantum algorithm that breaks these crypto primitives – at least not yet.
What’s the case for European standards?
Although the NIST is setting US standards, its actions are of worldwide concern. In fact, many global institutions are deeply involved in and contributing to NIST standardization work. In the EU, the European Union Agency for Cybersecurity (ENISA) has developed guidelines and recommendations fully aligned with NIST. Still, the question remains whether the EU will form one block or there might be country-specific differences. For the moment, certain government agencies – e.g., Germany’s Federal Office for Information Security (BSI) and the National Cybersecurity Agency of France (ANSSI) – stated they will support NIST-selected schemes but might extend the list of standardized algorithms with certain other algorithms.6 Outside of the EU, the UK’s National Cyber Security Centre (NCSC) is following the NIST’s standardization work closely. Its guidance for quantum-safe algorithms will follow the outcome of the NIST process, recommending specific algorithms for representative use cases.7
Regulatory compliance against national, supranational and industry-specific security standards will significantly influence the right timeline for each European business. Nevertheless, some organizations may wait (either deliberately or inadvertently) until they are obliged to act. The ETSI Quantum-Safe Cryptography specifications and the EU’s Cybersecurity and Cyber Resilience Acts will drive enterprise adoption of post-quantum security.
Now: Build an action plan
Even if fully published standards will not be available until 2024, companies should not wait until then to start on their PQC roadmap (see figure 3). Now that the initial recommendations have been released, there are common practices for businesses to follow, purchasing decisions to be made, and expertise to be developed to avoid future pain.

What to do then? First, build a well-considered strategy that appreciates the specifics of your enterprise, risks and stakeholders. Second, pragmatically and efficiently discover each instance of vulnerable encryption to be updated both in your enterprise and all the related ecosystems and supply chains it interacts with. Third, decide on a new crypto architecture. Fourth, begin the multi-year process of testing, implementing, and promulgating new quantum-resistant security throughout the extended enterprise.
A strong and proven strategy helps businesses find the delicate balance that’s needed between moving ahead and taking care to avoid introducing new risks. PQC deployments should initially run in parallel with current encryption methods, using post-quantum technology to add security on top of existing crypto systems (not dismantling them) where timing and resources permit.
In the new paradigm that is urgently needed to address the quantum security challenge, crypto agility presents itself as the best alternative. Setting a course for crypto agility will allow businesses to easily change the encryption method in case advances in cryptoanalysis threaten the viability of the adopted system as stated in Accenture’s latest piece, The race to crypto-agility.8
Leading European organizations are not waiting until 2024

Large European organizations across every industry are working on their post-quantum security agenda, not waiting until the release of 2024 standards to begin implementing solutions.
Financial institutions are first in line, since RSA-2048 and higher are standards in the conventional banking system. The Financial Services Information Sharing and Analysis Center’s (FS-ISAC) post-quantum cryptography working group is collaborating with global member institutions, including major European banks, to start implementing quantum-resistant measures as soon as possible.9 According to the World Economic Forum, Spain’s largest bank has started implementing cryptographic agility by developing “cryptography-as-a-service” to enable the bank to move services over to post-quantum cryptography.10
National governments are taking this threat seriously. The US National Security Agency (NSA) has already set itself a deadline of 2035, and has specified guidance and timelines.11 However, Europe is still behind in setting the deadline for this critical infrastructure’s migration. The experimentation phase, however, continues. The French Embassy in the United States, for instance, recently transmitted its first encrypted diplomatic message to Paris using post-quantum cryptography.12
The high-tech industry is also moving fast, since some devices that are produced today will potentially still be operating 10 years from now.
The same logic applies to the automotive industry. A connected vehicle lifetime of roughly 10 years means that a car developed today will likely still be on the road after 2032. One leading manufacturer of automotive components12 started revisiting the security of its vehicle component business almost a year ago, experimenting with PQC technology in various fields such as in-vehicle payment service, vehicle to everything (V2X) and an over-the-air (OTA) wireless solution.
The list of private and public organizations that have begun working with PQC is growing. Some industries such as health, financial services, communications, high-tech, government and automotive are advancing faster, but every single industry needs an action plan. As quantum machines continue to evolve, it is important to understand how they will impact cybersecurity, and when the threat could potentially materialize, based on each industry’s risk profile.
About the Authors
 Tom Patterson is Managing Director for Emerging Technology Security, Accenture, and the global lead for quantum and space security. He oversees the development of quantum security assets and teams that drive proven customized client solutions to defend against the coming quantum threats.
Tom Patterson is Managing Director for Emerging Technology Security, Accenture, and the global lead for quantum and space security. He oversees the development of quantum security assets and teams that drive proven customized client solutions to defend against the coming quantum threats.
 Laura Converso is a Thought Leadership Senior Principal for Emerging Technologies at Accenture Research. She focuses on technology incubation and innovation projects and leads the quantum computing research agenda.
Laura Converso is a Thought Leadership Senior Principal for Emerging Technologies at Accenture Research. She focuses on technology incubation and innovation projects and leads the quantum computing research agenda.
References
- Factoring integers with sublinear resources on a superconducting quantum processor https://arxiv.org/pdf/2212.12372.pdf
- M. Mosca, “Cybersecurity in an Era with Quantum Computers: Will We Be Ready?,” IEEE Security & Privacy, vol. 16, no. 5, pp. 38-41, September/October 2018 https://ieeexplore.ieee.org/document/8490169
- Ibid https://ieeexplore.ieee.org/document/8490169
- Cloud Security Alliance, Working Group: Quantum-safe Security https://cloudsecurityalliance.org/research/working-groups/quantum-safe-security/
- Computer Security Resource Center, PQC Standardization Process: Announcing Four Candidates to be Standardized, Plus Fourth Round Candidates, July 5, 2022 https://csrc.nist.gov/News/2022/pqc-candidates-to-be-standardized-and-round-4
- Robert Huntley, Post-Quantum Cryptography: Are You Ready?, EE Times, Europe, April 5, 2023 https://www.eetimes.eu/post-quantum-cryptography-are-you-ready/
- National Cyber Security Centre, Preparing for Quantum-Safe Cryptography, November 11, 2020 https://www.ncsc.gov.uk/whitepaper/preparing-for-quantum-safe-cryptography
- https://www.accenture.com/_acnmedia/PDF-145/Accenture-Crypto-Agility-POV-v7-0#:~:text=race%20for%20crypto%2Dagility&text=That%20means%20increasing%20flexibility%2C%20acquiring,for%20the%20entire%20supply%20chain.
- FS-ISAC, Preparing for a Post-Quantum World by Managing Cryptographic Risk, March 2023 https://www.fsisac.com/hubfs/Knowledge/PQC/PreparingForAPostQuantumWorldByManagingCryptographicRisk.pdf?hsLang=en
- World Economic Forum, Transitioning to a Quantum-Secure Economy, September 2022 https://www3.weforum.org/docs/WEF_Transitioning to_a_Quantum_Secure_Economy_2022.pdf
- Dan O’Shea, Quantum security experts are in step with NSA’s PQC timeline, Inside Quantum Technology, September 28, 2022 https://www.insidequantumtechnology.com/news-archive/quantum-security-experts-are-in-step-with-nsas-pqc-timeline/
- Ministère de l’Europe et des Affaires Étrangère, France transmits its first post-quantum cryptographic diplomatic message, December 1, 2022 https://www.diplomatie.gouv.fr/en/the-ministry-and-its-network/news/2022/article/france-transmits-its-first-post-quantum-cryptographic-diplomatic-message-1-dec
- Aju Business Daily, LG Electronics uses post-quantum cryptography technology for vehicle cyber security, October 5, 2022 https://www.ajudaily.com/view/20221005131500397



































