By Jessica Day
As the world moves towards a more flexible model of working, businesses are adopting new approaches to meet the changing needs of communication in the workplace. Remote working stands out as the most obvious example of this flexibility.
As an ancillary to remote work, businesses are now introducing different ways of working that help both employees and the establishment by cutting out what is often unnecessary red tape. Bring Your Own Device or BYOD is a practice of employees bringing their own devices including laptops, smartphones, and other gear to the workplace. It’s a practice that is rapidly gaining momentum, particularly among small businesses.
There are several variations of BYOD including BYOT (bring your own technology), BYOA (bring your own apps), and BYOL (bring your own laptop)
The immediate benefit of BYOD for small establishments is the savings they make in equipment costs. The benefit for employees is the convenience of working on their own machines, using tech that they’re comfortable with. However, BYOD can easily turn into an IT security nightmare leading to possible loss or theft of sensitive company data.
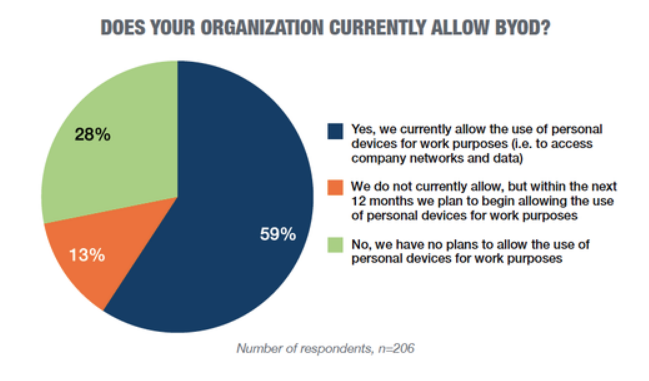
So what are some of the other pros and cons of having a BYOD policy?
Advantages of BYOD
- Enhanced Productivity – when employees have their personal devices they’re more likely to be logged on and available even outside of office hours because they’ll have constant access to their devices.
- Update – all tech requires regular updates. With personal devices, the onus is on the owner to keep with the latest updates.
Disadvantages of BYOD
- Unsecured Wi-Fi employees using their devices out of office can expose their devices to unsecured wi-fi connections leading to potential security threats from hackers.
- Employee Termination – if an employee leaves your organization, sensitive company data may still be stored on their personal devices, leading to a risk of potential data theft or sabotage.
In view of these risks, it’s important to have a good BYOD policy in place. A sound strategy provides both employees and businesses with guidelines for data protection and helps with lightening the load of compliance.
What Should a BYOD Policy Include?
This depends on the size of your company and the number of employees you have. Ideally, you should start by defining your objective for having a BYOD policy. This is what will shape your policy and form an introduction to the document. Let’s take a quick look at the BYOD approaches you could take.
Device Use at Work
It can be tricky to separate professional use from personal when an employee is using their own device. You can’t mandate everything. Still, you should have some control over what is acceptable to be accessed on personal devices when on the job. For example:
You could limit the personal use of devices during work hours. So whether it’s personal emails or messages, gaming, social media access, or reading-personal messages use should be restricted to a minimum during your stipulated work hours. Limiting distractions can help improve employee productivity.
In the same vein, some businesses implement a rule of accessing only company-sanctioned websites when using the company network. This is a security measure to ensure employees aren’t browsing unsecured sites through the business’s network and unconsciously exposing it to malicious malware. This is particularly relevant for businesses in the telecommunications sector like call centers that deal with large volumes of sensitive data.
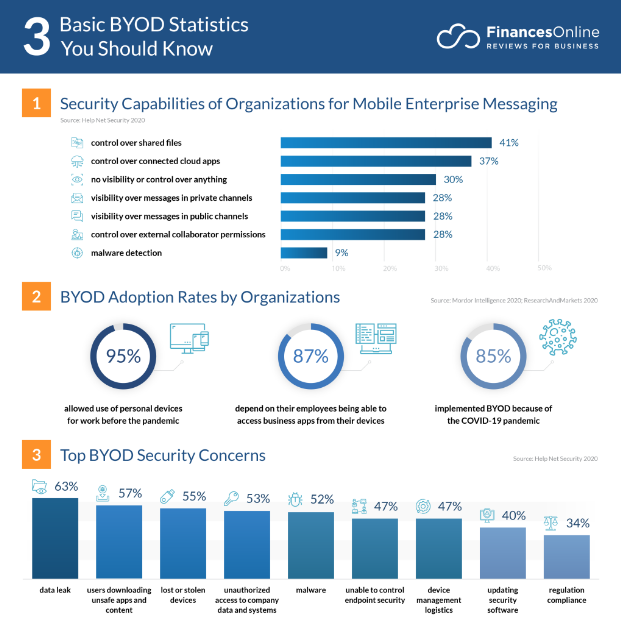
Restricting web browsing can be very effective for call center workforce management.
Some businesses restrict the use of cameras on personal devices during work hours for safeguarding the privacy of both the organization as well as employees.
Access, storage, and transmission of any illicit materials should be restricted, in addition to sharing sensitive company data.
To prevent any misunderstanding from ambiguity, businesses should ideally list the apps that are allowed to be downloaded on personal devices and those that aren’t. For example- some businesses restrict the download of apps outside Google Play Store and iTunes because their sources can’t be verified and so pose a potential security threat.
Type of Devices and Support
The challenge of digital transformation is that we’re not flooded with choices – from devices to software where there are hundreds of options to choose from. Once again, it’s a good idea to spell out exactly which devices and sometimes even more specifically, which brands are acceptable. Some businesses narrow this down to specific models and versions of operating systems.
Connectivity is the pillar on which remote working stands, so it’s crucial that everybody knows who to call when there’s a network issue. Make sure your BYOD policy clearly states which connectivity issues will or won’t be covered by the company IT. Also, ensure you have information about who to contact for hardware issues or any other problem with their operating system.
This could be your in-house IT, the manufacturer, or the employee’s local network carrier. What is important is your delegation of accountability.
Another important point to include in your BYOD policy is a mandate that all devices are configured by the company IT before they’re granted access to the company network.
Charges for Personal Devices
This is another difficult one. Normally, if you have a BYOD policy in place you wouldn’t compensate employees for their devices. It’s important to make the distinction between hiring devices and allowing employees to work on their own machines.
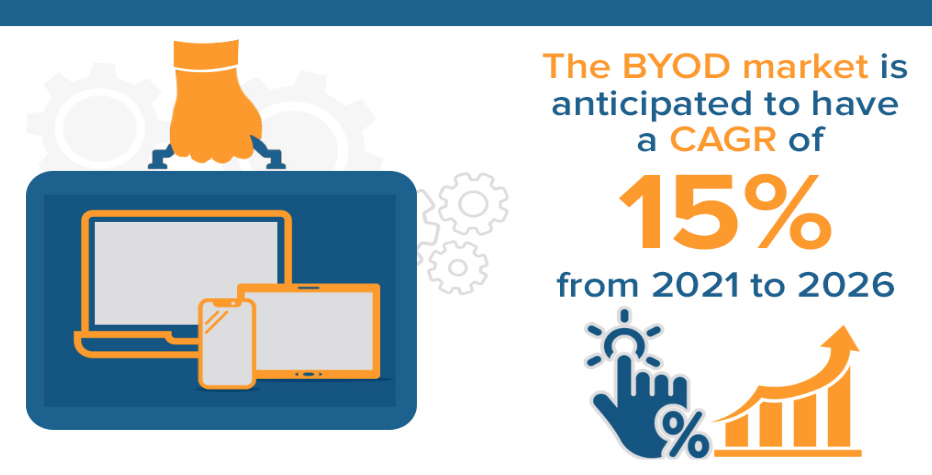
However, if you’ve introduced BYOD as a substitute for providing equipment, you should ideally offer some compensation. While drafting your BYOD policy you could include:
- Whether or not you will reimburse the employee for a percentage of the cost of their device.
- You should also clarify whether or not the company will directly pay an allowance to the employee to cover data costs – either a percentage or the entirety.
- Clarify whether or not the company will pay for installing additional software or applications. For example, your employees might need access to a certain workflow tool software for business process management, will your company pay for it?
- You should also specify the charges that the company will not reimburse like roaming fees.
Security
For any BYOD system to work, you need a solid security policy. Your BYOD policy would ideally mandate that all company-related assets be password-protected.
A good practice is to equip all devices with a “Find my Device” feature. This helps you track a missing device and can also be used to remotely wipe-clean a device. So in the event of a theft or damage to the device, any sensitive information stored on it can be remotely removed.
Another important statement in your policy should be about the regular updates of software, operating systems, and applications. A software or OS that shows an update notification is likely to have detected a security gap. These updates are therefore crucial for safeguarding system security.
Similar to the software updates, devices must install antivirus protection. Your company needs to specify if this is something they’ll provide or employees must purchase themselves. Either way, there are several affordable antivirus options on the market and they’re vital for protecting systems and networks from malware and other threats.
Businesses even without a BYOD policy should encourage a culture of regularly backing up data. If data is periodically backed up, it reduces the risk of it being lost as a result of theft or damage to the device.

Data Storage
This is partly linked to security. Businesses working remotely need a secure space to store data and most of them choose cloud-based storage solutions. These allow users to access, share and upload data from any device, anytime. Naturally, in a BYOD setting, cloud-based storage is the ideal solution.
MDMs or mobile device management solutions protect company data stored on employees’ personal devices. Whether it’s sensitive information about a new production test report stored on a personal device or your company’s quarterly sales forecast, MDMs can monitor, manage and secure devices being used in a business. MDMs can also remotely wipe data from a device if it’s lost or stolen.
Employee Termination
We discussed a BYOD policy while an employee is working at your company. But what happens to all the company data stored on their personal machines when they leave?
First off, you should accept the fact that some data like client contact details or any upcoming sales and marketing plans will remain with the employee even when they leave. You could take a proactive approach to this and make sure employees don’t download sensitive data to their personal devices. But this is not a foolproof measure.
For example- your company has a VoIP phone system for small businesses and all employees are asked to contact clients through this system only. There’s no guarantee that an employee will not retain a client’s contact details in spite of following this practice.
As part of your BYOD policy, you could also consider getting employees to sign non-disclosure agreements. Should you plan to wipe their personal devices when they leave, make that clear from the start.
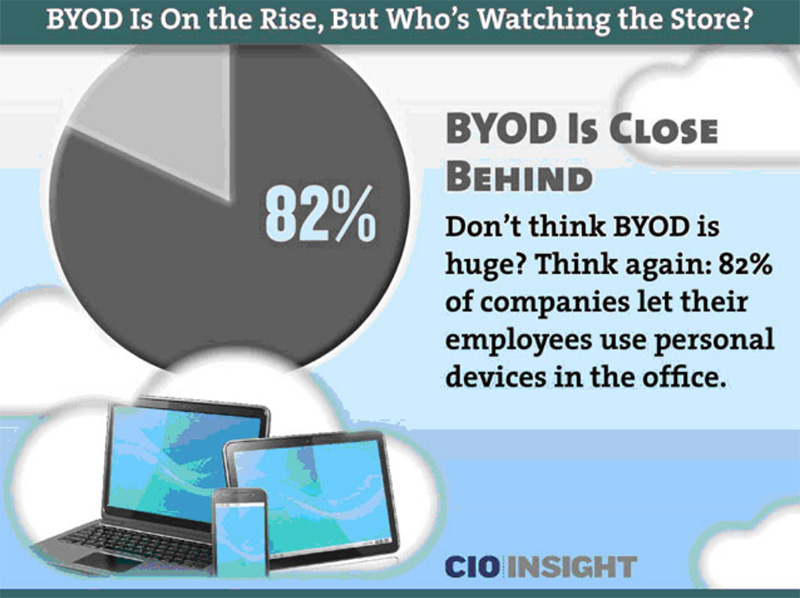
To Sum Up
BYOD can be a great way for small businesses to get started without bearing large upfront costs in purchasing equipment. It could well become one of the key aspects to influence business transformation.
It also provides freedom of choice for employees to work with tech that they’re used to. But for this practice to work you need a robust BYOD policy to prevent any misuse and to optimize productivity.
About the Author

Jessica Day is the Senior Director for Marketing Strategy at Dialpad, a modern business communications platform with call center IVR that takes every kind of conversation to the next level—turning conversations into opportunities. Jessica is an expert in collaborating with multifunctional teams to execute and optimize marketing efforts, for both company and client campaigns.


































